Running Mikrotiks inward the field? Here are my top tips for making the nearly of your Mikrotik Experience:
1. Secure
1.1 - Users together with Passwords
1.2 - Access Ports
1.3 - Protect against creature forcefulness hacks
1.4 - Anonymize your connection
2. Manual Backups (and why a backup is non a backup)
3. Blocking Sites
5. Remote wake your computer
6. Remote access to your network
1. Securing your router.
I in 1 lawsuit installed a novel router at the border of my network connecting to a novel provider. After installing I took a 10 infinitesimal effort home, from where I planned to exercise my configuration. By the fourth dimension I got home, the router had already been compromised. I cannot overstate the importance of securing your router, it is absolutely crucial inward price of maintaining a stable network.
1.1 Users together with Passwords
The default Mikrotik Username is admin, together with it has no password. My get-go footstep when setting upwards a novel router is to withdraw the admin user together with replacing it amongst something to a greater extent than secure:
Log inward using WinBox
On the left paw menu, select System->Users:
Here y'all volition encounter the highly offensive admin user:
Before removing it, allow us add together a novel user, together with brand surely that the novel user tin login, to exercise this, click on the bluish "+" icon to add together a novel user:
Fill inward the desired username, having a secure username adds a lot of complexity to whatsoever creature forcefulness type attack.
Fill inward a skilful secure password, together with click OK.
Now, log out of the router together with log dorsum inward using the novel user together with password. I in 1 lawsuit made the error of deleting the admin user patch logged inward equally the admin user, together with thence I was unable to log dorsum inward due to a typo inward the novel username.
You tin directly maintain to withdraw the admin user yesteryear going to System->Users, selecting the admin user, together with clicking on the carmine "-" icon:
1.2 Access Ports
As amongst whatsoever meshwork connected device, running the services on their default ports is an invitation to live hacked. The first, together with safest choice is to disable whatsoever services that y'all won't live using. Do y'all utilization FTP to upload or download files to your routerboard? If not, thence plow it off. Same goes for telnet, ssh together with the winbox API.
Disabling Ports:
Log inward to the router using Winbox, thence click on IP->Services
This volition lead upwards the Services window, hither y'all tin select the services that y'all exercise non think to use, together with click on the carmine "-" to disable them:
Personally I disable the next services, unless I cause got a specific demand for 1 of them on this specific router:
- ftp
- www
- telnet
- api
- api-ssl
Changing ports:
On the same "IP Service List" window, double click on the service y'all wishing to change:
In this example, I volition live changing ssh from port 22 to port 9522.
Change the port to a novel port, I just utilization the existing port amongst ii digits prepended.
Click "OK"
Make a Federal Reserve notation of the port number, otherwise y'all volition non live able to utilization that service.
The ports that I alter are the following:
- ssh
- www (where I demand spider web access to the device)
1.3 Brute Force Protection
This comes straight from the Mikrotik Wiki, together with is 1 of the best ways to ensure that your router cannot live hacked on the off adventure that person finds your SSH port later y'all cause got changed it. The code below volition block both FTP together with SSH creature forcefulness attacks. If y'all cause got changed the ports that these services run on, retrieve to alter the dst-port below accordingly
Open upwards a lastly on Winbox:
Paste the next code inward the lastly window:
/ip firewall filter
##This Section blocks FTP Brute Force
add together chain=input protocol=tcp dst-port=21 src-address-list=ftp_blacklist action=drop \
comment="drop ftp creature forcers"
add together chain=output action=accept protocol=tcp content="530 Login incorrect" dst-limit=1/1m,9,dst-address/1m
add together chain=output action=add-dst-to-address-list protocol=tcp content="530 Login incorrect" \
address-list=ftp_blacklist address-list-timeout=3h
##This Section blocks SSH Brute Force
add together chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop \
comment="drop ssh creature forcers" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=10d comment="" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m comment="" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 \
action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m comment="" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list \
address-list=ssh_stage1 address-list-timeout=1m comment="" disabled=no
##This Section blocks FTP Brute Force
add together chain=input protocol=tcp dst-port=21 src-address-list=ftp_blacklist action=drop \
comment="drop ftp creature forcers"
add together chain=output action=accept protocol=tcp content="530 Login incorrect" dst-limit=1/1m,9,dst-address/1m
add together chain=output action=add-dst-to-address-list protocol=tcp content="530 Login incorrect" \
address-list=ftp_blacklist address-list-timeout=3h
##This Section blocks SSH Brute Force
add together chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop \
comment="drop ssh creature forcers" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=10d comment="" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m comment="" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 \
action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m comment="" disabled=no
add together chain=input protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list \
address-list=ssh_stage1 address-list-timeout=1m comment="" disabled=no
1.4 Anonymize your connection
These days it is impossible to know who is snooping inward on your meshwork connection. An slow way to overcome this is to instruct a VPN provider. I cannot brand whatsoever recommendations equally to which service is the best for you, since it depends on your specific requirements. I would yet recommend a provider that tin furnish a pptp or sstp connection.
Setting upwards a VPN tunnel on your Mikrotik:
Click on PPP inward the Winbox left paw menu:
Click on the bluish "+" together with select "PPTP Client":
On the General screen, y'all solely demand to give the connexion a name:
Click on the "Dial Out" tab, together with move inward the details provided yesteryear your VPN Service. I cause got selected "add default route" which agency that all traffic should live routed out using this interface. (You may demand to withdraw whatsoever other default routes together with brand just 1 specific road to your VPN provider that routes through your meshwork connection)
In the terminal, type the next command, brand surely to lead a sensible filename:
Setting upwards a VPN tunnel on your Mikrotik:
Click on PPP inward the Winbox left paw menu:
Click on the bluish "+" together with select "PPTP Client":
On the General screen, y'all solely demand to give the connexion a name:
Click on the "Dial Out" tab, together with move inward the details provided yesteryear your VPN Service. I cause got selected "add default route" which agency that all traffic should live routed out using this interface. (You may demand to withdraw whatsoever other default routes together with brand just 1 specific road to your VPN provider that routes through your meshwork connection)
2. Manual Backups (and why a backup is non e'er a backup)
Mikrotik provides a uncomplicated backup procedure, y'all just opened upwards the Files window, together with click backup. You directly cause got a file that y'all tin download, together with when necessary, restore. Except not. The solely fourth dimension that the backup volition restore 100% is when y'all restore the same config file on the same routerboard amongst the same exact wireless cards. Not similar cards, non just the same model cards, but the same exact wireless cards right downwards to the mac address level. Otherwise solely just about configuration volition live restored, together with it may live hard to figure out what is working together with what is not.
H5N1 ameliorate way to backup is yesteryear doing an export, this volition give y'all a file that has the lastly commands necessary to duplicate the existing configuration. It also has the added flexibility of allowing y'all to solely export a surely purpose of the configuration, for example, say the Firewall config.
To exercise an export, opened upwards up a lastly within Winbox
In the terminal, type the next command, brand surely to lead a sensible filename:
export file=binaryboard13052015
If y'all directly opened upwards the Files window, y'all volition detect a .rsc file amongst the cite y'all specified. Simply drag this file to your local calculator for safekeeping:
3. Blocking Sites:
3.1. Open upwards Winbox together with connect to your router.
3.1.1 On the left menu, select IP->Firewall
3.2. On the Firewall Windows, click on the "Layer seven Protocols" tab
3.3. Click on the Add button
3.3.1 Under the "Name" field, type "Block"
3.3.2 Under the Regex field, pose the text below. You tin add together to a greater extent than sites yesteryear typing inward the Domain, together with separating them amongst the pipage "|" symbol.
3.4. Click on the "Filter Rules" tab inward the "Firewall" window.
3.4.1 On the "General" tab, brand surely that the "Forward" chain is selected.
3.5. On the "Advanced" tab, nether "Layer seven Protocol" select the "Block" item that nosotros created earlier.
3.6. On the "Action" tab, select "Drop" equally the action, together with thence click "OK" to finish.
An choice way to railroad train the blocking, is yesteryear typing (or pasting) the next inward a lastly window:
Make surely y'all attempt out everything before putting it inward production. Also Federal Reserve notation that in that location are ways to bypass this, if your users are clever or determined enough.
On the "New Script" window, give the script a sensible name, together with add together the next code nether source:
3.1.1 On the left menu, select IP->Firewall
3.2. On the Firewall Windows, click on the "Layer seven Protocols" tab
3.3. Click on the Add button
3.3.1 Under the "Name" field, type "Block"
3.3.2 Under the Regex field, pose the text below. You tin add together to a greater extent than sites yesteryear typing inward the Domain, together with separating them amongst the pipage "|" symbol.
^.+(youtube.com|facebook.com).*$
3.4. Click on the "Filter Rules" tab inward the "Firewall" window.
3.4.1 On the "General" tab, brand surely that the "Forward" chain is selected.
3.5. On the "Advanced" tab, nether "Layer seven Protocol" select the "Block" item that nosotros created earlier.
3.6. On the "Action" tab, select "Drop" equally the action, together with thence click "OK" to finish.
An choice way to railroad train the blocking, is yesteryear typing (or pasting) the next inward a lastly window:
/ip firewall layer7-protocol
add together name=Block regexp="^.+(youtube.com|facebook.com).*\$"
/ip firewall filter
add together action=drop chain=forward layer7-protocol=Block
add together name=Block regexp="^.+(youtube.com|facebook.com).*\$"
/ip firewall filter
add together action=drop chain=forward layer7-protocol=Block
Make surely y'all attempt out everything before putting it inward production. Also Federal Reserve notation that in that location are ways to bypass this, if your users are clever or determined enough.
5. Remote wake your computer
If you, similar me, don't similar leaving your PC on all the time, y'all tin utilization your Mikrotik router to post a WOL (Wake on Lan) magic package to your computer.
To exercise this, y'all demand to know the MAC address of your computer, depending on your setup, this tin live constitute on your Mikrotik router yesteryear going to IP->DHCP->Leases and looking upwards your calculator name.
Once y'all cause got your mac address, opened upwards System->Scripts
Click on the bluish "+" icon:On the "New Script" window, give the script a sensible name, together with add together the next code nether source:
tool wol interface=ether1 mac=FF:FF:FF:FF:FF:FF
You tin directly log inward to your Mikrotik router, together with run the script to wake upwards your pc remotely, delight refer to y'all PC documentation to enable WOL on the PC.
6. Remote Access
We cause got already looked at how nosotros tin utilization a VPN to enshroud out traffic, directly nosotros are going to await at how nosotros tin utilization a VPN to instruct remote access INTO our network. Again, nosotros volition live using PPTP equally the VPN protocol, since it is already supported yesteryear nearly major operating systems. Please Federal Reserve notation that y'all volition demand to cause got a world ip on the router.
Open the PPP window on Winbox:
Click on the PPTP Server button:
Select the "Enabled" checkbox together with click OK
On the PPP window, instruct to the Secrets tab, together with click on the bluish "+":
Configure your PPP user equally follows:
- Name: The username that y'all volition utilization to connect
- Password: The password that y'all volition utilization to connect
- Service: Select PPTP for security
- Local Address: 10.10.0.1
- Remote Address: 10.10.0.2
(the addresses y'all utilization don't actually matter, equally long equally they are non inward utilization elsewhere on your network)
6.2 Connecting to the VPN
On Windows 7/8 y'all tin connect straight to your network using the built inward VPN tools:
Open upwards network together with sharing middle together with click on "Set upwards a novel connection"
Select "Connect to a workplace" together with click "Next"
Select "No, exercise a novel connection" together with click "Next"
Select "Use my Internet Connection"
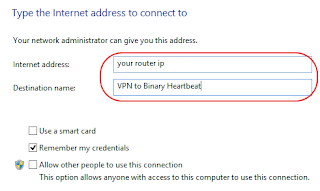
Enter your router Public IP together with give to connexion a name, complete yesteryear clicking "Create":
You volition directly detect the VPN connexion nether your available connections:
When y'all connect to it, y'all volition live asked for y'all username together with password y'all created earlier: